Why DEFENDERBOX?
Nine out of ten German companies have been target of a cyberattack in recent years. In order to prepare for possible compromises, Bitkom e.V. recommends that over 90% of corporate cyber defense must be carried out in advance. External players should be involved for comprehensive protection measures. Proactive security tools such as the DEFENDERBOX.
Why DEFENDERBOX?
Nine out of ten German companies have been target of a cyberattack in recent years. In order to prepare for possible compromises, Bitkom e.V. recommends that over 90% of corporate cyber defense must be carried out in advance. External players should be involved for comprehensive protection measures. Proactive security tools such as the DEFENDERBOX.
The DEFENDERBOX is the indispensable tool for an effective cyber security strategy for IT companies. Your advantages:
The DEFENDERBOX is the indispensable tool for an effective cyber security strategy for IT companies. Your advantages:

Cost efficiency
Early warning system:
Identifying security vulnerabilities before they can be exploited by attackers is particularly important for an industry that is becoming increasingly digitally networked.
Reporting &and prioritization:
Clear, comprehensible reports with prioritized recommendations for action enable targeted and efficient security measures.

User-friendly

Comprehensive protection
It continuously scans the entire network for security vulnerabilities.

Maximum flexibility
& scalability
Regardless of whether you are a small start-up or a large IT company. We manage the pentests and your requirements. So that you can feel secure again!

Cost efficiency
Early warning system:
Identifying security vulnerabilities before they can be exploited by attackers is particularly important for an industry that is becoming increasingly digitally networked.
Reporting &and prioritization:
Clear, comprehensible reports with prioritized recommendations for action enable targeted and efficient security measures.

User-
friendly

Comprehensive protection
It continuously scans the entire network for security vulnerabilities.

Maximum flexibility
& scalability
Regardless of whether you are a small start-up or a large IT company. We manage the pentests and your requirements. So that you can feel secure again!

AI-supported
Threat detection
This is how we ensure a proactive defense against both new and known threats.

Simple installation
& commissioning
This minimizes the effort and cost of implementation.
No IT or cyber know-how required.

Automated
Identification of gaps

Regular updates
& maintenance
This means you always receive the highest possible protection.

AI-supported
Threat detection
This is how we ensure a proactive defense against both new and known threats.

Simple installation
& commissioning
This minimizes the effort and cost of implementation.
No IT or cyber know-how required.

Automated
Identification of gaps

Regular updates
& maintenance
This means you always receive the highest possible protection.

Fast response times

Personal
support
cybersecurity team
So that you feel safe again.

Fast response times

Personal
support
cybersecurity team
So that you feel safe again.
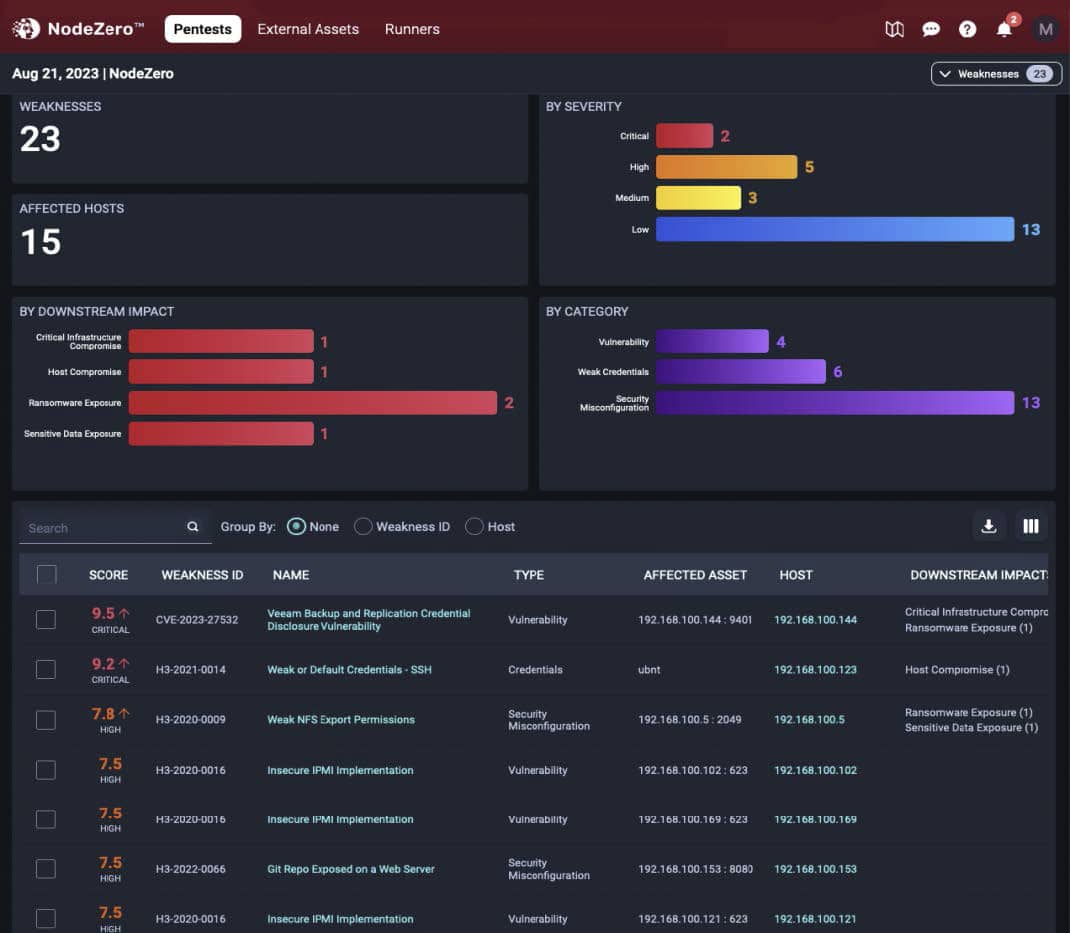
Reporting on the attack paths provides information on vulnerabilities.
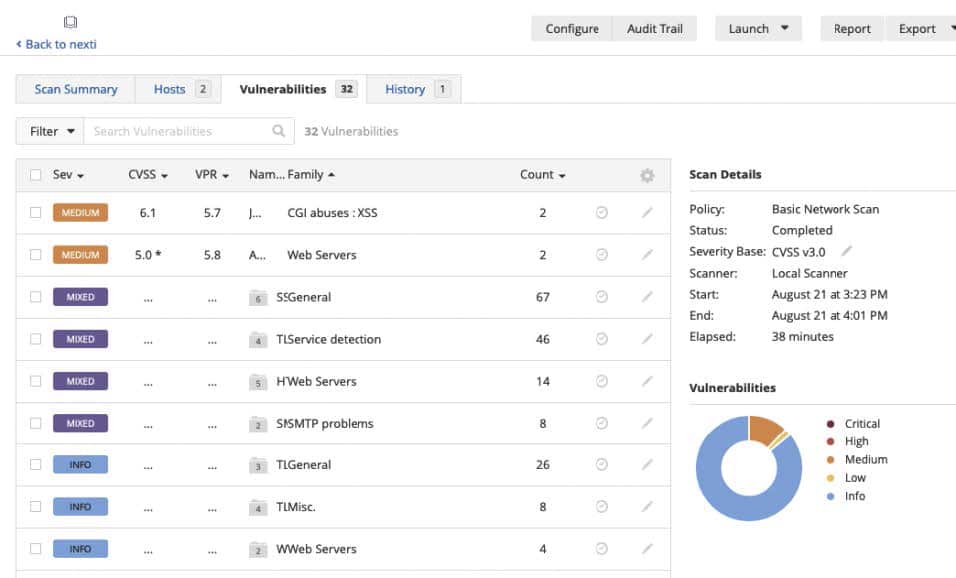
Pentest summary for an optimal overview
DEFENDERBOX bundles the know-how from security checks of more than 1000 servers and the experience from vulnerability analyses of more than 2 million telecommunications customers.
So hackers don't stand a chance!
DEFENDERBOX bundles the know-how from security checks of more than 1000 servers and the experience from vulnerability analyses of more than 2 million telecommunications customers.
So hackers don't stand a chance! The interior of the DEFENDERBOX is checked before each use and adapted to the current status of your existing security software and measures in order to achieve optimum results.

IT infrastructure and technology
IT security
"Cybersecurity for IT companies needs to be redefined. Our DEFENDERBOX should be part of this. Because then you know your cybersecurity is at the highest level."
Markus Schulte,
Security Expert & Managing Director SMB Cybersecurity GmbH

IT infrastructure and technology
IT security
"Cybersecurity for IT companies needs to be redefined. Our DEFENDERBOX should be part of this. Because then you know your cybersecurity is at the highest level."

