NIS-2 "Network and Information Security" Directive
With the NIS 2 Directive, mandatory security measures and reporting obligations will apply to many companies and organizations in 18 critical sectors from October 2024. This includes many SMEs that were not previously affected. This NIS2 replaces the NIS Directive from 2016 with the aim of achieving a better common level of cybersecurity in the EU.
Compared to the previous NIS Directive, NIS-2 greatly expands the group of affected companies, the obligations and the official supervision. Violations of the NIS2 Directive can even result in heavy fines.
Who is affected?
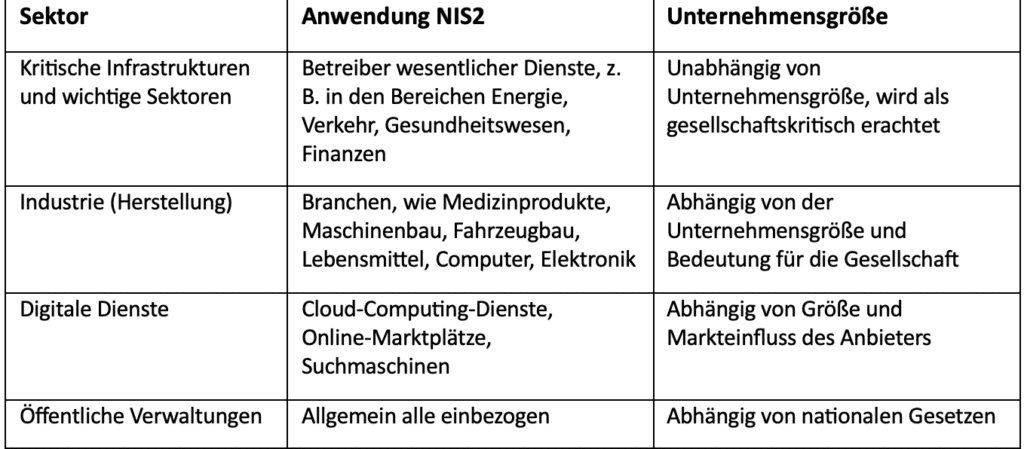
Public and private entities in 18 sectors with at least 50 employees or at least EUR 10 million in annual turnover and annual balance sheet total. All of these entities carry out their activities in the EU. In addition, the following entities, regardless of their size, are also covered by the NIS2 Directive:
- Providers of public electronic communications networks or publicly available electronic communications services
- Trust service provider
- TLD name registries and DNS service providers (except operators of root name servers)
- Sole providers that are essential for society and the economy
- Facilities whose failure would have a major impact on public order, safety or health
- Facilities whose failure could lead to a systemic risk with cross-border consequences
- Facilities that are critical due to special national or regional importance
- Central government public administration body defined by the EU Member State or critical public administration body at regional level
- Critical infrastructures according to Directive (EU) 2022⁄2557
- Entities providing domain name registration services
The new directive also applies indirectly to service providers and suppliers of affected facilities.
Cybersecurity measures a MUST
The following cybersecurity measures must be implemented by companies:
- Policies: Concepts for risk analysis and security for information systems
- Incident response: Detecting, analyzing, containing and responding to incidents
- Business continuity: backup management and recovery, crisis management
- Supply chain: Security in the supply chain
- Purchasing: Security in the acquisition, development and maintenance of IT systems, including management and disclosure of vulnerabilities
- Effectiveness: Evaluation of the effectiveness of the risk management measures
- Cyber hygiene, training: Cyber hygiene (e.g. updates) and training in cyber security
- Cryptography: Use of cryptography and encryption where appropriate
- Personnel, access, assets: personnel security, access control and asset management
- Authentication: multi-factor authentication or continuous authentication
- Communication: Secure voice, video and text communication, including in an emergency if necessary
CRITIS
NIS-2 is a further development of existing security measures that are already anchored in many companies through ISO standards legislation such as the KRITIS Regulation or the Security Act 2.0. With the introduction of NIS2, a Europe-wide harmonization of these standards will now be achieved, building on the efforts and investments already made by companies.
Even if you are not affected as an SME, cybersecurity is an issue that should be prioritized by management: Because as a managing director, you are liable and, as a small and medium-sized enterprise, you are also faced with the tricky task of making the right level of investment in appropriate infrastructures.
What is the state of cyber security in your company?


Current contributions
- Over 80% critical security vulnerabilitiesAlarming results from our IHK cooperation on IT security at companies! Which critical security gaps were found in our pentests?
- "Find & Fix" campaign to get to know each otherProtect your company and find out which security gaps or vulnerabilities exist in your IT.
- New DEFENDERBOX featureAfter each pentest (penetration test) with the DEFENDERBOX, our customers receive an email informing them of the status of the result.
- DEFENDERBOX NIS-2 compliantOur DEFENDERBOX is NIS-2 compliant, i.e. the DEFENDERBOX reports document exactly all pentests that are valid as NIS-2 certification for the NIS-2 audits.
- Targeted by cyber criminalsIf law firms fall victim to blackmail cyber attacks, the damage is particularly high. This is why ransoms are often paid. Investments in cyber security and insurance offer protection.

Do you want to know how secure your company is? Try it out! Click here for a test installation of DEFENDERBOX.
The trial offer is valid until
30. September 2024.
Pingback:DEFENDERBOX NIS-2 compliant - DEFENDERBOX