Why DEFENDERBOX?
Do you know whether your SME is adequately protected against cyber threats? Is your IT infrastructure protected against automated hacker attacks? Do you know the vulnerabilities that cyber criminals could exploit to penetrate your network?
By using DEFENDERBOX, you can identify precisely these security gaps and vulnerabilities quickly, easily and cyber securely. So that you feel secure again!
Why DEFENDERBOX?
Do you know whether your SME is adequately protected against cyber threats?
The DEFENDERBOX identifies security gaps and vulnerabilities. So that you feel secure again:
Maximum CYBER SECURITY for your SME! Your advantages:

Highest
accuracy
So that you feel safe again!

Fast
results
Largest
coverage

Low
expenditure

Highest
accuracy
So that you feel safe again!

Fast
results

Largest
coverage

Low
expenditure

Effective
Pentesting
With DEFENDERBOX, thousands of algorithms scan for vulnerabilities and security gaps in your IT.

From the perspective of
hackers
Artificial intelligence is used - against artificial intelligence.
Penetration-
testing
You receive a precise analysis of all risks, including prioritization of remediation.
Software
as-a-Service
Your penetration tests (pentests) and scans are initiated fully automatically.
Additional cyber security options can be booked on a modular basis.

Effective
Pentesting
With DEFENDERBOX, thousands of algorithms scan for vulnerabilities and security gaps in your IT.

From the perspective of
hackers
Artificial intelligence is used - against artificial intelligence.

Penetration-
testing
You receive a precise analysis of all risks, including prioritization of remediation.

Software
as-a-Service
Your penetration tests (pentests) and scans are initiated fully automatically.
Additional cyber security options can be booked on a modular basis.
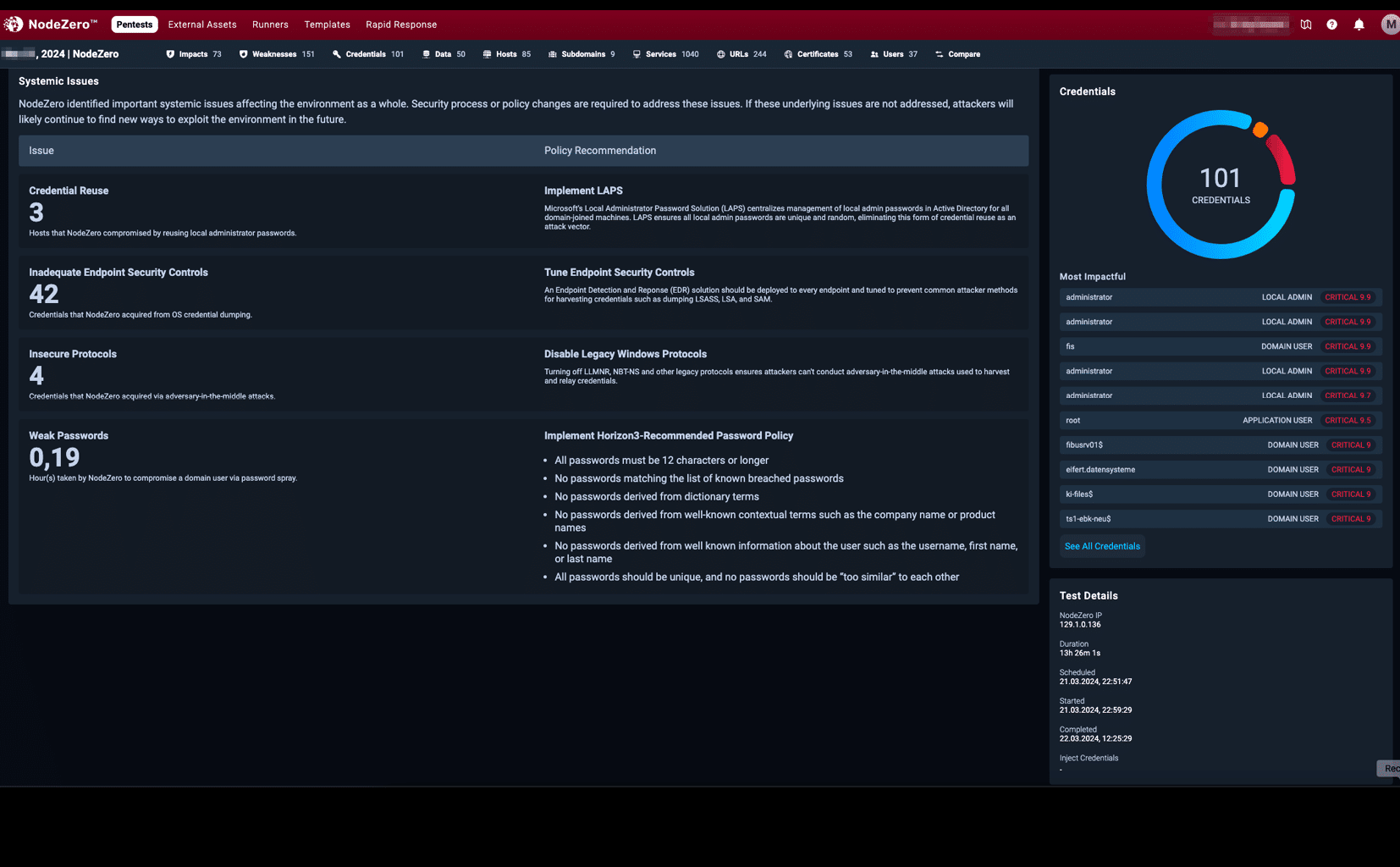
Are employee accounts compromised?
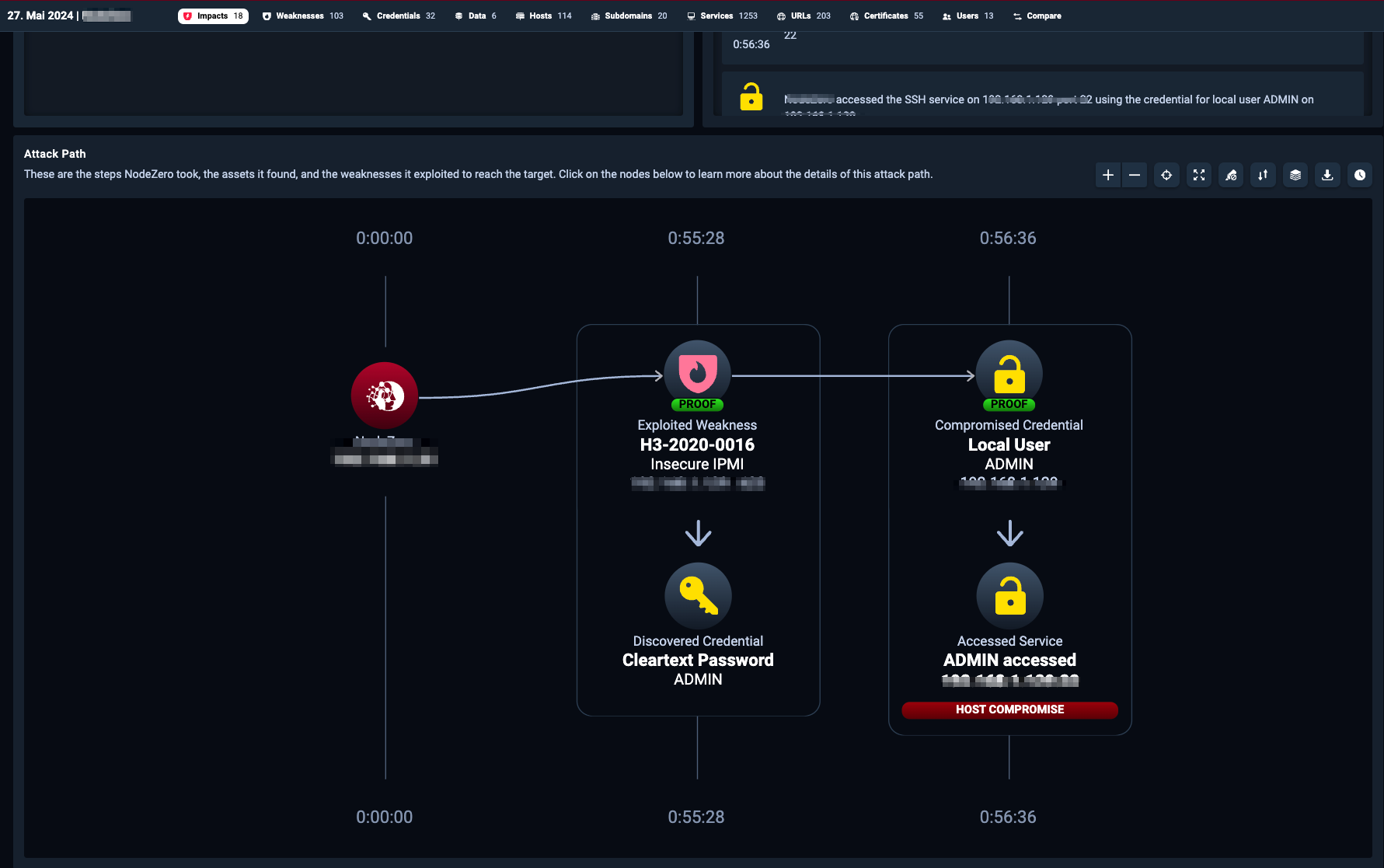
Your attack path analysis
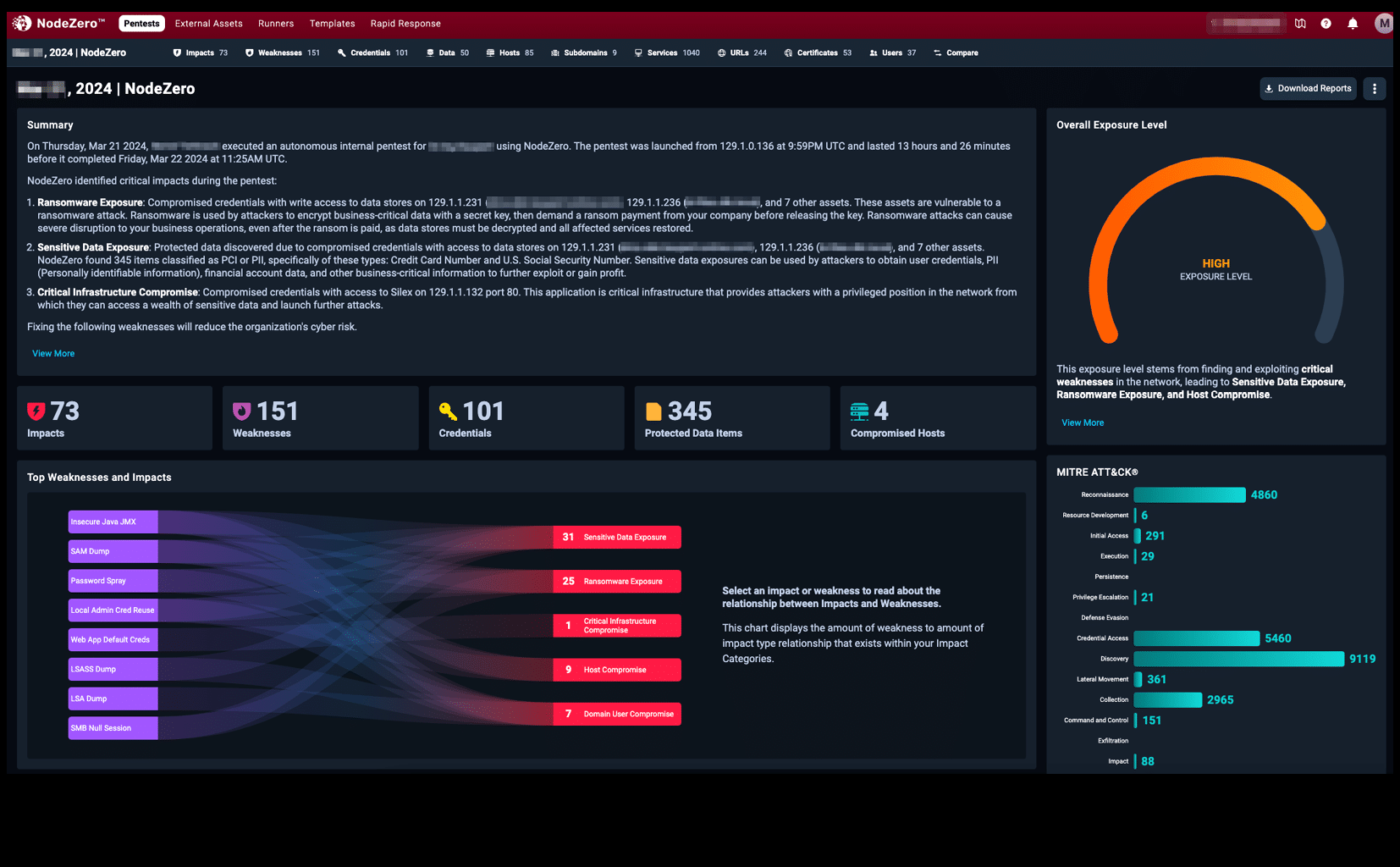
Weak points and effects are described in detail in your report.
PROTECTION.
The DEFENDERBOX checks hundreds of different attack scenarios during each pentest. At the same time, it identifies security gaps in your network.
REPUTATION.
DEFENDERBOX protects your reputation by eliminating downtime as compromised vulnerabilities can be detected and closed before a real threat occurs.
ADVANCE.
You can use the results and evaluations to proactively optimize your security structure and measures.
AUTOMATED.
The penetration test starts fully automatically on a weekly or monthly basis.


DEFENDERBOX bundles the know-how from security checks of more than 1000 servers and vulnerability analyses of more than 2 million telecommunications customers.

IT infrastructure and technology
IT security
"Hackers will always be one step ahead. That's why every company needs proactive and regular monitoring in addition to technical security."
Markus Schulte,
Security Expert & Managing Director SMB Cybersecurity GmbH

IT infrastructure and technology
IT security
"Hackers will always be one step ahead. That's why every company needs proactive and regular monitoring in addition to technical security."

